

Vitae dignissim curabitur nascetur nullam fermentum conubia dolor sagittis habitant habitasse ut etiam
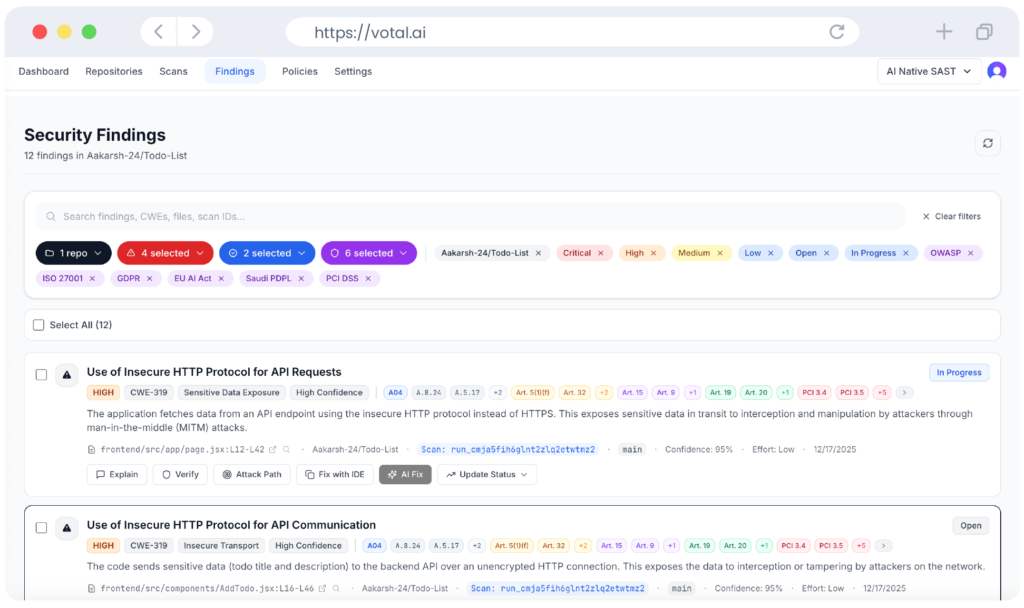
Traditional SAST tools generate noise.
Our AI-native engine delivers high-confidence, developer-trusted findings that scale across enterprise codebases.
Significantly reduced false positives vs rule-based SAST
Faster remediation cycles across large engineering teams
Actionable security insights mapped to real exploit paths


-> Semantic modeling of large, distributed codebases
-> Cross-service and cross-repo visibility
-> Context-aware data flow analysis
-> Business logic and authorization flaw detection
-> Prioritized by exploitability and impact
-> Precise fix recommendations
-> Minimal noise, maximum trust
-> CI/CD and SDLC integration
Shift-left security without slowing development
Risk-based prioritization for large portfolios
Consistent enforcement of secure coding standards
Leading Enterprises
Threat Detection Rate
Continuous Monitoring
